Hi welcome to first my blog post, so bare with me if things might seem a little out of place, we all start somewhere.

My name Andre but my online tag is 0ffDre. This post will be describing my journey building a pwnagotchi and all the issues I ran into. Coming out of this you’ll get a better understanding of this rasp pi project. Let’s start with, what is pwnagotchi?

What is a Pwnagotchi:
I constructed a Pwnagotchi utilizing a Raspberry Pi 0 W, an e-ink display, and a Pisugar (external battery). This device employs an ‘AI’ powered by bettercap, a portable framework written in Go for recon and attacking Wi-Fi, Bluetooth, ethernet networks, and wireless HID devices.
The AI’s primary function is to learn from the surrounding WiFi environment, actively seeking and capturing crackable WPA key material. It can go through both active and passive sniffing. Active sniffing is done by executing authentication and association attacks, a process that involves sending deauthentication packets to devices. Passive sniffing is done by not sending to deauth packets, but waiting for a handshake to end and try and capture, less aggressive but also less reliable.
The captured material is saved as a PCAP (Packet Capture) files, a standard format for storing network traffic data. These PCAP files contain valuable information, including full and half WPA handshakes, as well as PMKIDs. The next step involves using tools like hashcat and aircrack-ng to attempt to decrypt those captured handshakes and bruteforce techniques until.
Deauthentication attacks, a vital part of this process, involve sending specially crafted packets to disrupt the connection between a client device and an access point. This forces the client to re-authenticate, providing an opportunity for Pwnagotchi to capture the necessary handshake data.
It’s worth noting that the success of these operations depends on various factors, including the strength and complexity of the targeted WiFi password.
Ok so now that we have a chatgpt answer of the background software for pwnagotchi. But how does the Pwnagotchi utilize the bettercap software? The pwnagotchi displays this information with fun and friendly faces, while sorta illegally throwing devices off their wifi connection (depending on state and juristication). Always get consent to perform these educational projects, I highly suggest trying to capture your home wifi, it will be easier to crack your wifi, as you know your own wifi’s passwords….hopefully.
Some Faces and meanings:
| (⇀‿‿↼) sleeping | The starting face, occasionally will also take naps when changing wifi channels. |
| (°▃▃°) intense | Pwny is sending an association frame to an access point in order to force it to leak the PMKID (PMKID contains the hash of the PSK). |
| (╥☁╥ ) sad | If there are no friendly units around and the amount of consecutive inactive epochs reached. |
| (⌐■_■) cool | The unit is deauthenticating a client station from an access point. |
| ( ⚆_⚆),(☉_☉ ) observing (neutral mood) | This face is when your pwnagotchi is waiting and observing what bettercap can find on all the channels it’s hopping through. |
| (◕‿‿◕) awake/normal | – This face is the neutral awake status of the unit. |
| (ب__ب) lonely | This face is displayed when your pwnagotchi loses contact with another pwnagochi, or if the amount of missed interactions with access points or client stations. |
| Possible Plugins for your Pwnagotchi: | There are an assortment of different plugins you can use to help cracking or collecting pcaps. As well as different ways to customize your pwnagotchi, like darkmode great me to, want a different background than the default, different faces, the list is very long. Here is a few, more can be found on the community discords and websites: https://github.com/wpa-2/pwnagotchi-plugins | – Make tweets on twitter/X about recent activities your little pwny is doing. – Storing them in your google drive. – Christmas countdown timer. -Confirming that the pcaps captured contain a full handshake or PMKID otherwise it will delete it. |
Now that we have a good idea on what a pwnagotchi is, lets understand what goes into a pwnagotchi. Here is a list of the items I purchased and used to build the wifi munching machine.
| Pre-soldered Raspberry Pi Zero: The brains of the operation this is what the small computer that will process the bettercap, initialize any responses for the pwnagotchi, pretty much runs the whole show. I opted for a pre-soldered Pi board, as I did not have either the skills nor the tools to solder the headers on. But if your skilled for it go right ahead, might even be cheaper. Link: amazon-link-RaspPi0 wh |  |
| Waveshare-eink display V3: This is what will display or what the pwnagotchi will be displayed on. This is a lite-weight display board that consumes little power. It also keeps the last image displayed when powered off, so your pwny can keep smiling when turn off. -Note* sometimes different versions are delivered, and later steps call for this information. I ordered a v2 but got a v3. Keep this in mind before you start to trouble shoot. Link: Waveshare eink display |  |
| SD and SD reader: This is how we will install our pwnagotchi, flashing all the files onto our rasp pi 0w. |  |
| Micro USB: You need a cable to be able to ssh into your pwny and transfer data, utilize plugins, also a method to power your pwnagotchi. |  |
| Pi-Sugar 3: This is an accessory, it’s nice to be able to carry your pwny around with you on the go. Note* the conductors on (spring loaded pins that touch the rasp pi0) the board can fall off. I’ve had to replace a pisugar due to my carelessness putting it into my 3d case. There are cheaper and other versions of the pi sugar. Also there are plugins out there to display battery percentage and other features. |  |
| Pwnagotchi 3D-Printed Case: This website has different 3d models that you can use to protect your pwny. You don’t want to hurt your pwny do you? | https://www.yeggi.com/q/pwnagotchi/ |
| Cracking Tool: I used aircrack-ng I will provide a small tutorial of using my home wifi’s pcap file and password to crack my wifi. |  |
| Resources that can be used: | CyberspacemanMike, githubs, unofficial pwnagotchi community, plugins, aircrack-ng, hashcat. |
| Materials: | Raspberry Pi 0W (pre-soldered header), waveshare-eink display v3, micro-SD, micro-SD reader, type-c data cable, pi-suger, 3d-case: https://www.yeggi.com/q/pwnagotchi/. |
| Getting Started: | If you gathered the materials and you’re ready to being building your very own little pwnagotchi. I followed cyberspace for most of the steps, I also used different resources for troubleshooting different discords: CyberspacemanMike: https://cyberspacemanmike.com/ https://www.youtube.com/@cyberspacemanmike Unofficial Pwnagotchi Discord Community: https://discord.gg/PgaU3Vp Official Pwnagotchi Website: https://pwnagotchi.ai/ Note* There are many instruction videos out there, a lot are outdated. That is why I recommend Cyberspacemanmike’s instructions, more in-depth and up to date. |
| Initial Steps: | Instead of trying to explain step by step how to install the pwnagotchi img and flash it onto your SD card etc… I would say to just follow Cyberspacemanmike’s tutorials. He notes different errors that can occur, whether its a driver issue, incorrect model, etc… Utilize the discords/communities for troubleshooting or questions, or message me on linkedIn: https://www.linkedin.com/in/andre-richard23/ |
Once you have a few pcaps ethically obtained and you want to try and crack them. We can use Aircrack-NG to throw a wordlist like rockyou or darkcode at our handshakes. You have to extract the files from your pwny and run aircrack against them with a wordlist. Im using kali linux as it already has rockyou pre-installed.
| Here is the command to run aircrack against your pcap files: | 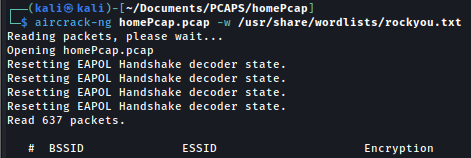 |
| Once you hit enter it will perform a dictionary attack against your pcap files using the rockyou.txt wordlist. In my case I put my password in rockyou to expediate the process. | 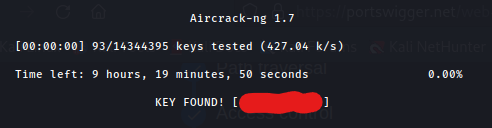 |
